1. You can’t encrypt systems
If you are operating a network the applications and configurations that define that network need to be decrypted to run. Look at the Target compromise. It was caused not by a lack of encryption, what caused the breach which was an attack on integrity – a compromise of the credit card database configuration(s), machine reader software, and security layer components) that led to the loss of credit card information. Malware and viruses are integrity attacks – and if you don’t have integrity you are left with no choice but to search for vulnerabilities, equivalent to looking for needles in a haystack.
Guardtime’s answer: If you have integrity you have real-time situational awareness for every stalk of hay. Knowledge is power. With this real-time awareness, real-time incident response, real-time data-loss prevention, investigation, and/or network resilience it is now possible to detect and react to any misconfiguration, network and/or component/application failure. Privacy is what you get when you have integrity.
See how we achieve this here. By instrumenting a system with immutable digital twins, one for each networked digital asset, you are no longer searching - you have a level of certainty around the state of your network that has never been possible before
2. You can’t audit encryption
Ebay’s announcement last week is fascinating to read:
“After conducting extensive tests on its networks, the company said it has no evidence of the compromise resulting in unauthorized activity for eBay users, and no evidence of any unauthorized access to financial or credit card information, which is stored separately in encrypted formats.”
Here’s our question: How exactly do they know? Can they prove it? Despite all the advances in technology over the last 40 years digital forensics hasn’t advanced much since the 1980s. The status quo for forensics is still for an investigator to use imaging tools and try and figure out what happened after the fact. This ex post facto nature of evidence collection is extremely unreliable. Due to the volatile nature of electronic data any hacker worth his salt knows how to delete logs or worse, manipulate logs to cover his tracks and attribute his activity to an innocent party, which is why attribution of crimes on the Internet is so hard, whether a 16 year-old manipulating school records, a nation-state attack on critical infrastructure or cybercriminals hacking into Ebay’s network.
Guardtime’s answer: If you have integrity – i.e. if you can have independent verification of everything that happens in your network then you, your auditors and forensic investigators don’t need to guess. For more information see here
3. Encryption gives you a false sense of security
On May-30th 2011 it was reported in the press that Lockheed Martin, the U.S. government’s top information technology services provider, was hacked. The attack has been characterized as a “fairly subtle”, yet “significant and tenacious” attack on servers at its massive Gaithersburg, Maryland data center, located not far from the company headquarters in Bethesda. Reports from the press indicate that the hackers appeared to have gained entry using information stolen in a separate, even more audacious attack on one of the world’s highest profile security firms: RSA. Reports indicate that the attackers were able to steal the private keys used for creating RSA SecurID tokens. Here’s the point – if the world’s leading security firm can’t manage their keys what chance do the rest of us have – your local hospital managing patient records or your local power station?
Guardtime’s answer: If you have integrity – i.e. if you can have real-time verification that your network is in a clean-state then you can assume compromise – and mitigate attacks in real-time whenever an intruder’s acts compromise the integrity of the network. For more information see here
4. Encryption doesn’t work against the Insider Threat
Encryption as security is only as good as the security of the credentials used to access the data. Let’s look at the activities of Edward Snowden. Encrypting the data didn’t work. He didn’t need to defeat the encryption, he simply needed to compromise the credentials of the administrators who had access to the encrypted data, which he did with great gusto.
Guardtime’s answer: If the network had integrity i.e. if Snowden had known that deleting the logs (to help cover up his tracks), would have triggered an integrity compromise he would not have been able to commit his act – he would have been forced in to good behavior. The only way to defeat insiders intent on mayhem is make them know that they will be caught. You can’t prevent crime but you can be 100% effective in detecting it.
5. Data Integrity is the biggest threat in cyberspace
Don’t take our word for it:
“The most serious national security threat looming in cyberspace may be the potential for vital data to be altered by cybermarauders, according to a cyber expert with the Office of the Director of National Intelligence (ODNI).
Speaking to an attentive audience at the AFCEA Global Intelligence Forum in the National Press Club in Washington, D.C., Sean Kanuck, national intelligence officer for cyber issues at the National Intelligence Council in the ODNI, admitted that the threat to data integrity keeps him awake at night.”
- Robert K. Ackerman, SIGNAL Online, July 31, 2013
“The nation’s top military officer said the United States lacks a strategy for cybersecurity, and data integrity remains one of the biggest security concerns for the Defense Department.
Speaking today at a conference on disruptive military technologies, sponsored by the Atlantic Council, Joint Chiefs Chairman Gen. Martin Dempsey warned the nation remains unprepared for a major cyber-attack."
Let’s face it if you want to take out a country you don’t need to steal secrets. You simply need to manipulate the software inside their power-grid, communications and transport systems and it’s game-over. These are integrity attacks and the reality is there is not a single network out there has integrity – i.e. the administrators can prove they are in a clean state. They might be, they might not – they simply don’t know.
Guardtime Answer: see here.
6. You can’t prove encryption security is working
As we’ve mentioned encryption just means you are one credential compromise away from the data. Let’s take patient records as an example. A sophisticated state actor could compromise an administrator’s credentials, access (decrypt) the data, change your blood type, encrypt it again and delete the evidence of their activity. Then boom, you’re dead and nobody has a clue what happened.
The arrogance of the Silicon Valley encryptionistas here is stunning – ‘encrypt everything’ is their mantra, but then what? Pray?
Guardtime Answer: Yup you guessed it - start with integrity.
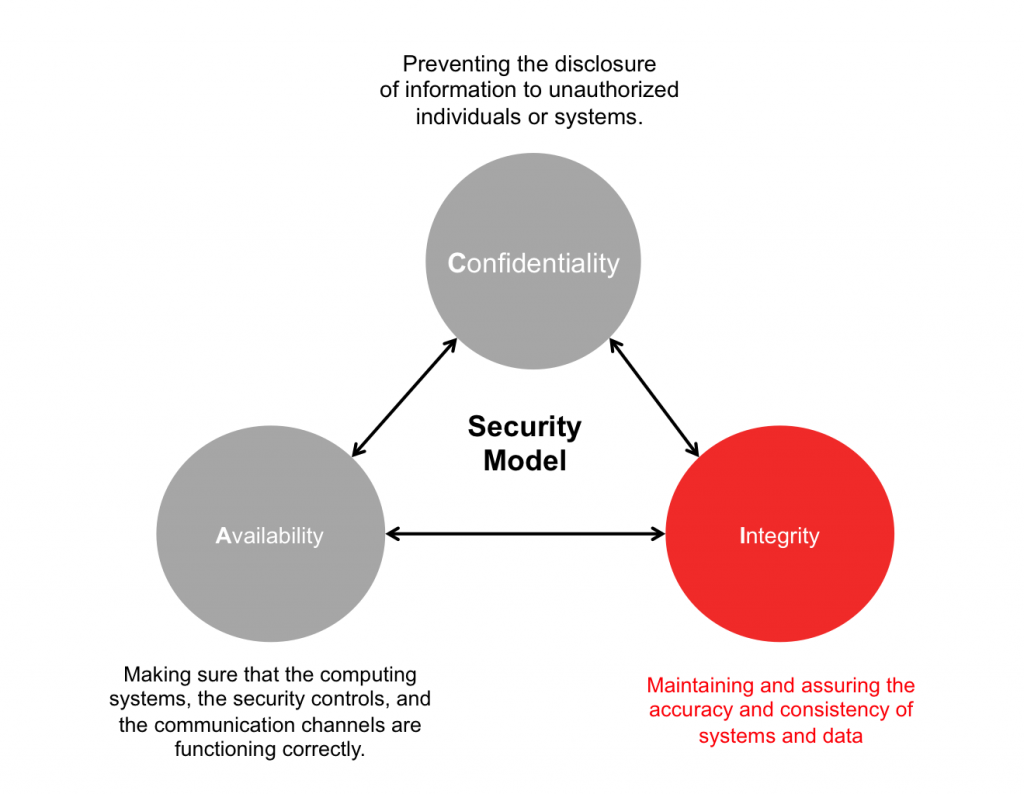
What is Integrity ?
Integrity is the big gaping hole in security today. Without it, encryption is worse than useless, bringing a false-sense of security which almost always leads to downfall.
Integrity brings auditability and transparency of evidence to governance frameworks that allows the citizen, public, and private sector to mutually audit each other’s activities in accordance with an agreed upon governance framework. Estonia solved it. Less obfuscation – more integrity and irrefutable transparent evidence to independently verify and begin to trust the transaction and identity interactions on the network.
You don’t need encryption to have integrity. In fact confidentiality and integrity are inversely proportional (why can you be certain that Spain won the last world cup? Reason: over a billion people watched it live, the event was widely witnessed. Nobody doubts the integrity of the result and there was nothing confidential about it) Of course it could have been a mass cover-up and actually the Democratic People’s Republic of Korea really won the event but the cost of implementing such a cover-up makes it practically impossible.
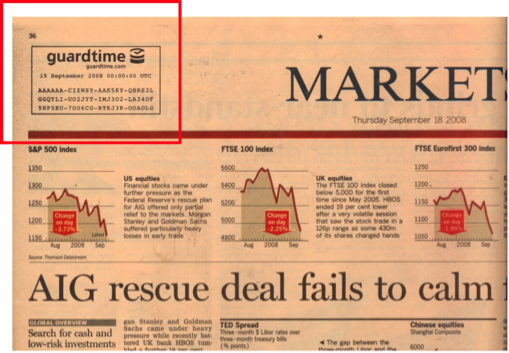
Estonia has taken the same principle for systems. That number published in the Financial Times represents proof of everything that happened in Estonian digital society.
A short history of Estonian digital society
No keys, no encryption just mathematical proof of everything that happened. Estonia solved the integrity problem by using less confidentiality, less obfuscation, instead irrefutable transparent evidence to independently verify and enable trust in the transaction and identity interactions on their networks.
By integrating KSI into networks every component, configuration, and digital asset can be tagged, tracked, and located with real-time verification no matter where that asset is transmitted or stored.
Subsequently with this real-time awareness, real-time incident response, real-time data-loss prevention, investigation, and/or network resilience it is now possible to detect and react to any misconfiguration, network and/or component/application failure. Privacy is what you get when you have Integrity.
Conclusion
Guardtime’s mission is to provide transparency for the world’s information. US President Barack Obama recently said that you can’t have 100% security, 100% privacy and zero inconvenience.
At Guardtime we agree. You can however have 100% transparency and accountability, across all networks for all citizens and their respective Government institutions that serve and protect them.